ITDR 2.0 for MSPs
“+1 for Petra. So far ahead of the other players in the space… they have no competition”
“I’ve done head-to-head comparisons — Petra was twice as fast. In a world where speed matters most, that’s the key differentiator.”
“I have to tell you! You have an amazing product––better than any other ITDR products out in the market.”
"My customers are really impressed at the speed and the visibility of the incident, and the reports are crystal clear. Thank you Petra!"
“Petra's advanced machine learning has helped us stop multiple attacks with no false positives. We believe this will make a substantial reduction in the workload of our SOC team and reduce noise and alert fatigue.”
“We've really enjoyed working with Petra, it's helped us open doors with larger enterprises and showcase how our team can deliver value beyond what their current providers offer.”
“Petra detected and quarantined within 2 minutes. What else can I say? Petra made us look like heroes. Thanks for building an amazing product.”
“If you manage Microsoft environments, you should be using Petra”
“We have been absolutely loving them compared to Blackpoint cloud response. They’ve been blowing it out of the water.”
“We've been using Petra for a number of months and have been very happy! Much faster and more accurate than the other solutions we've used”
If you're an MSP managing Microsoft environments, you should be using Petra.
The secret weapon of high-growth MSPs
The Problem:
Attacks are way up,
and way harder to catch.
“We used both Blackpoint and Huntress, but Petra is so far the only real solution to the massive increase in BECs we are seeing.”




.webp)
Alerts cost time.
Slow response costs trust.
support

"Now, it's all just handled.”

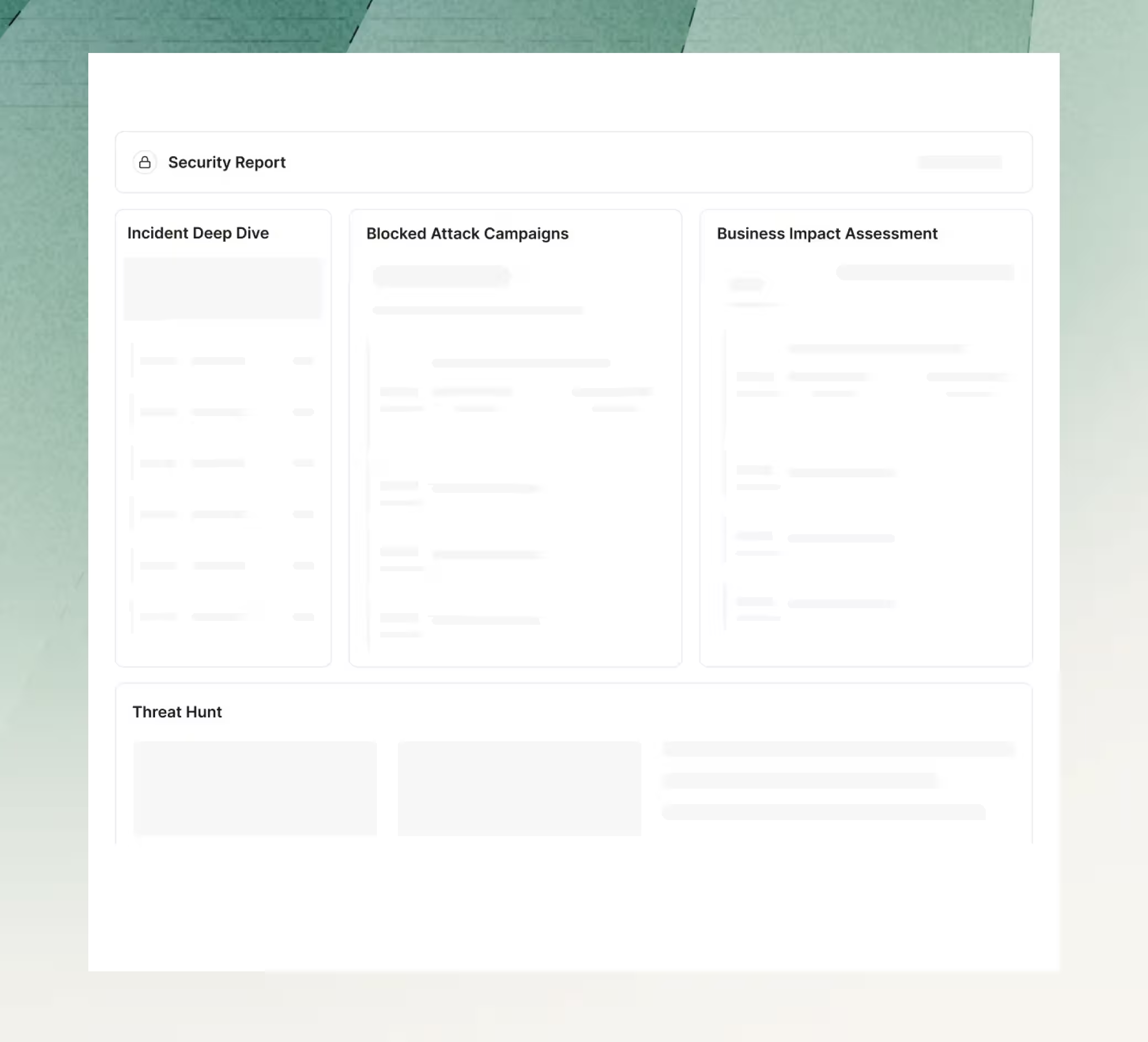
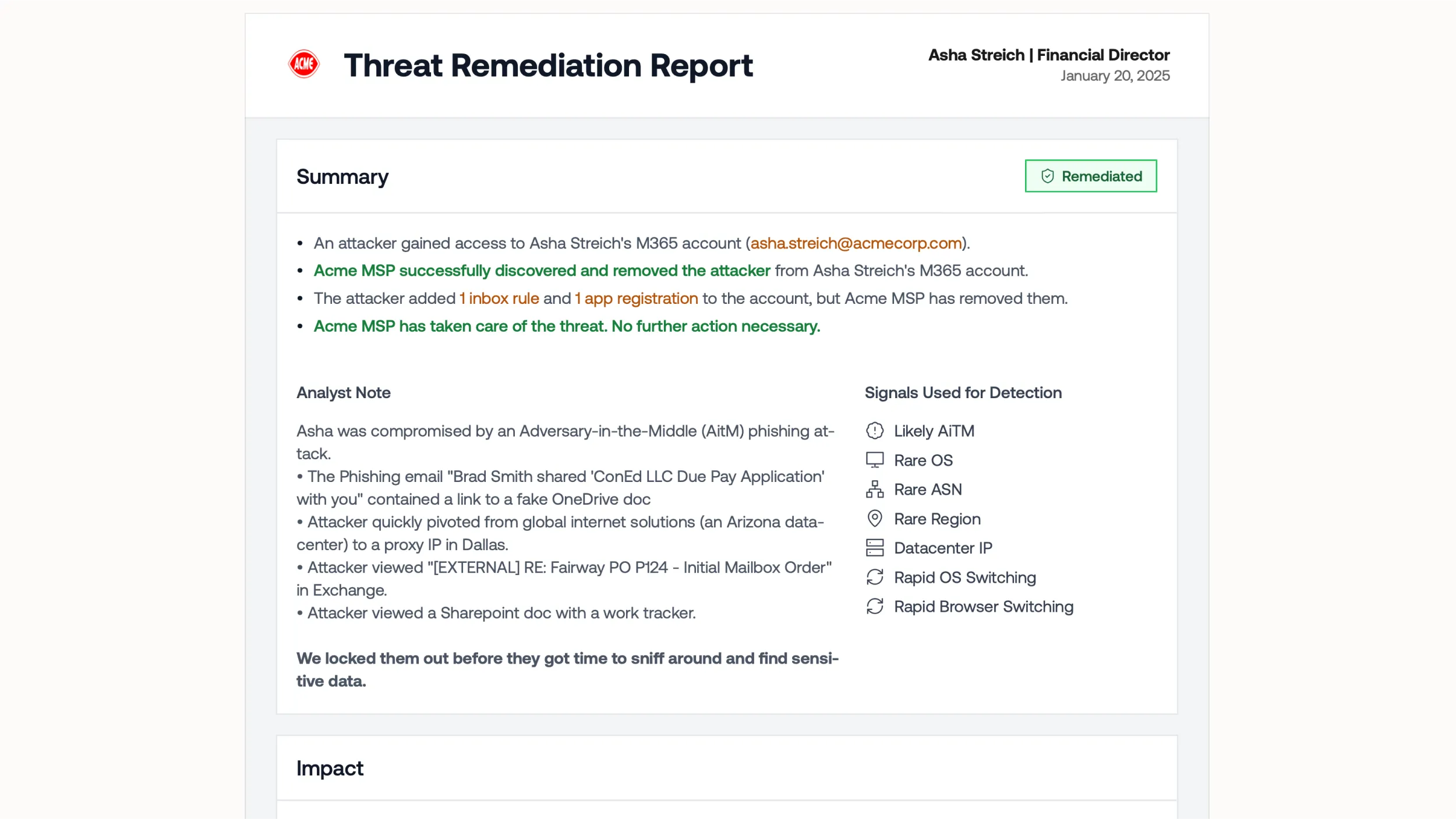
ITDR
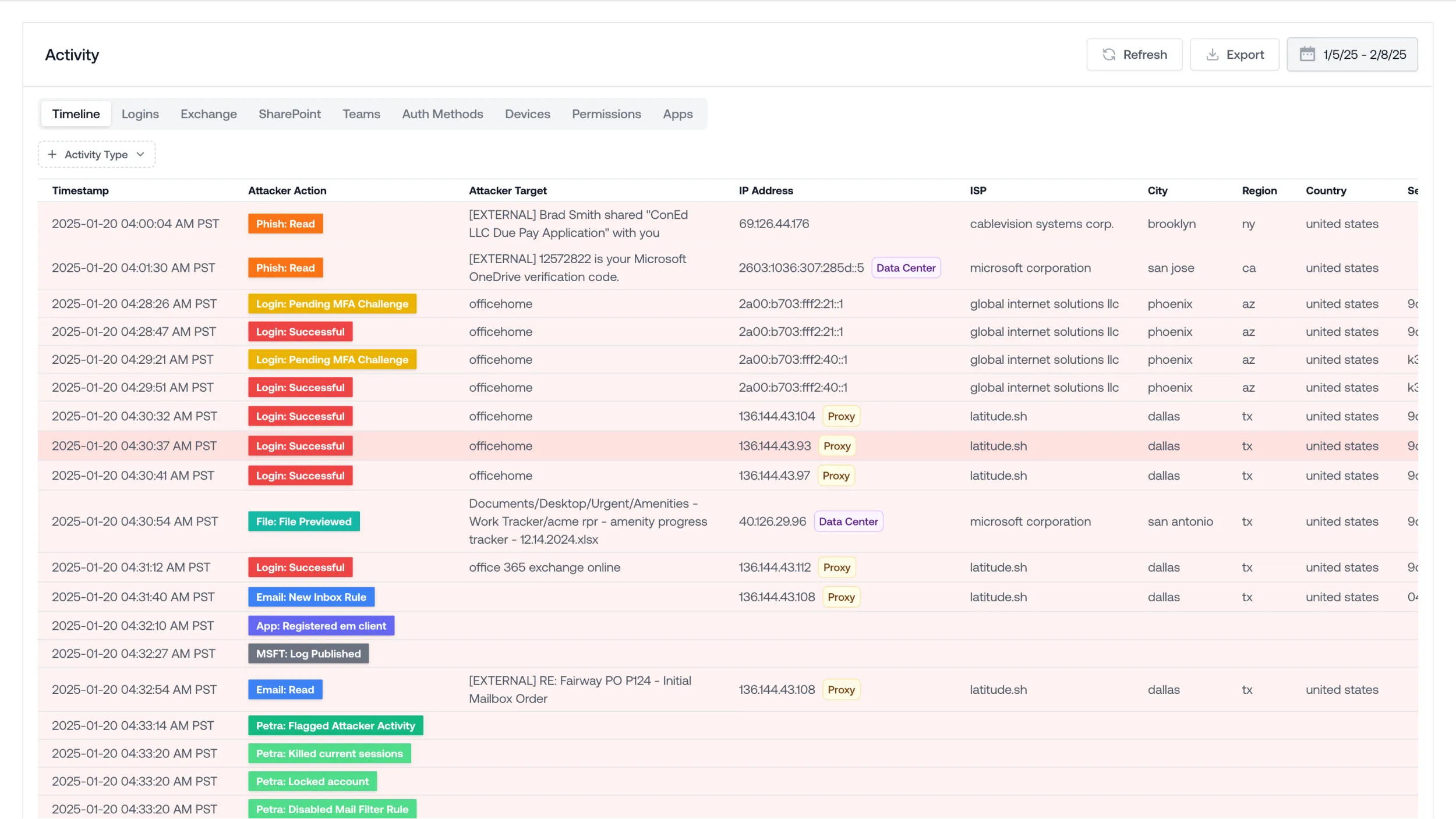
Catch Attacks Faster
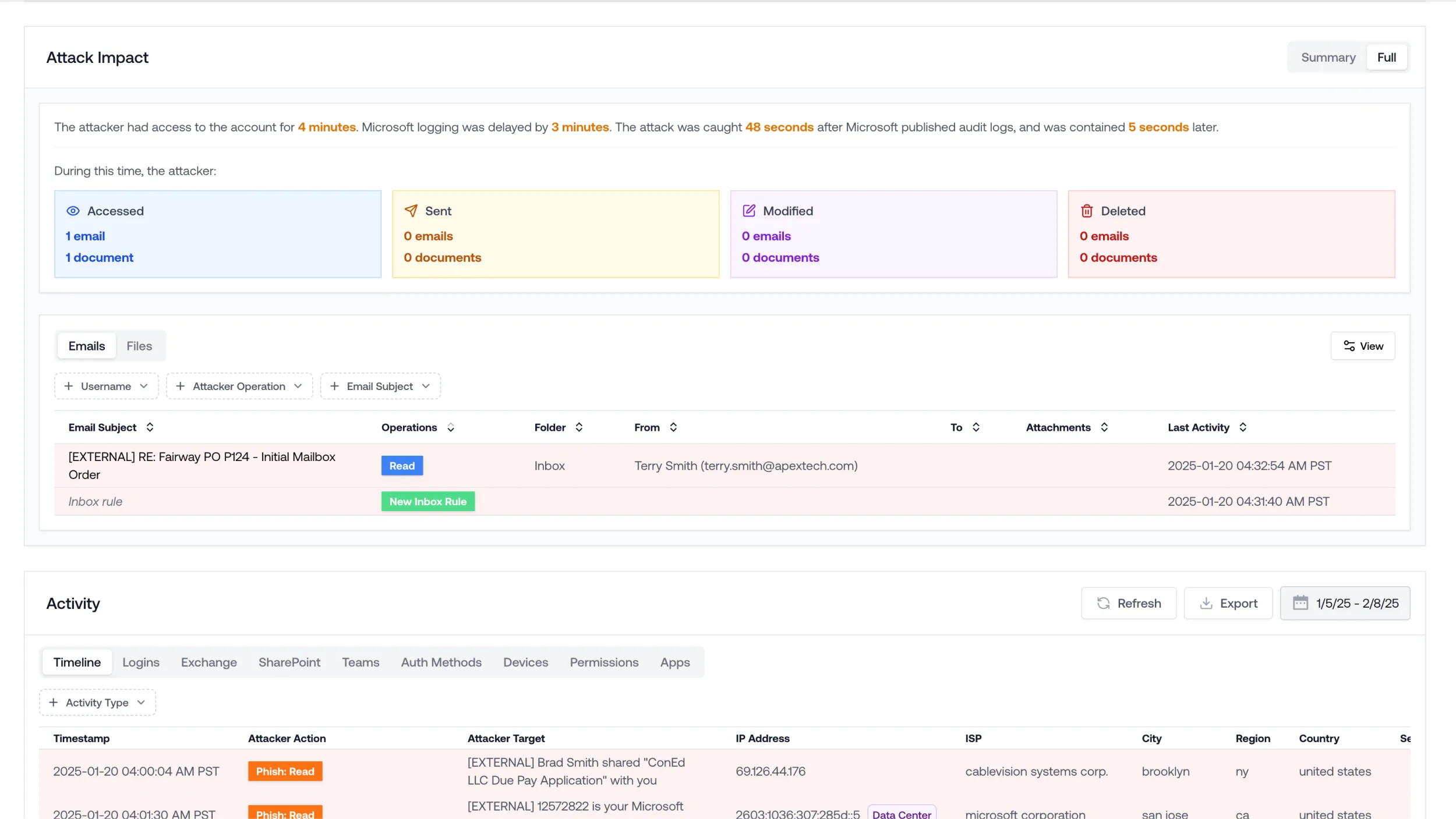
Understand the Attack
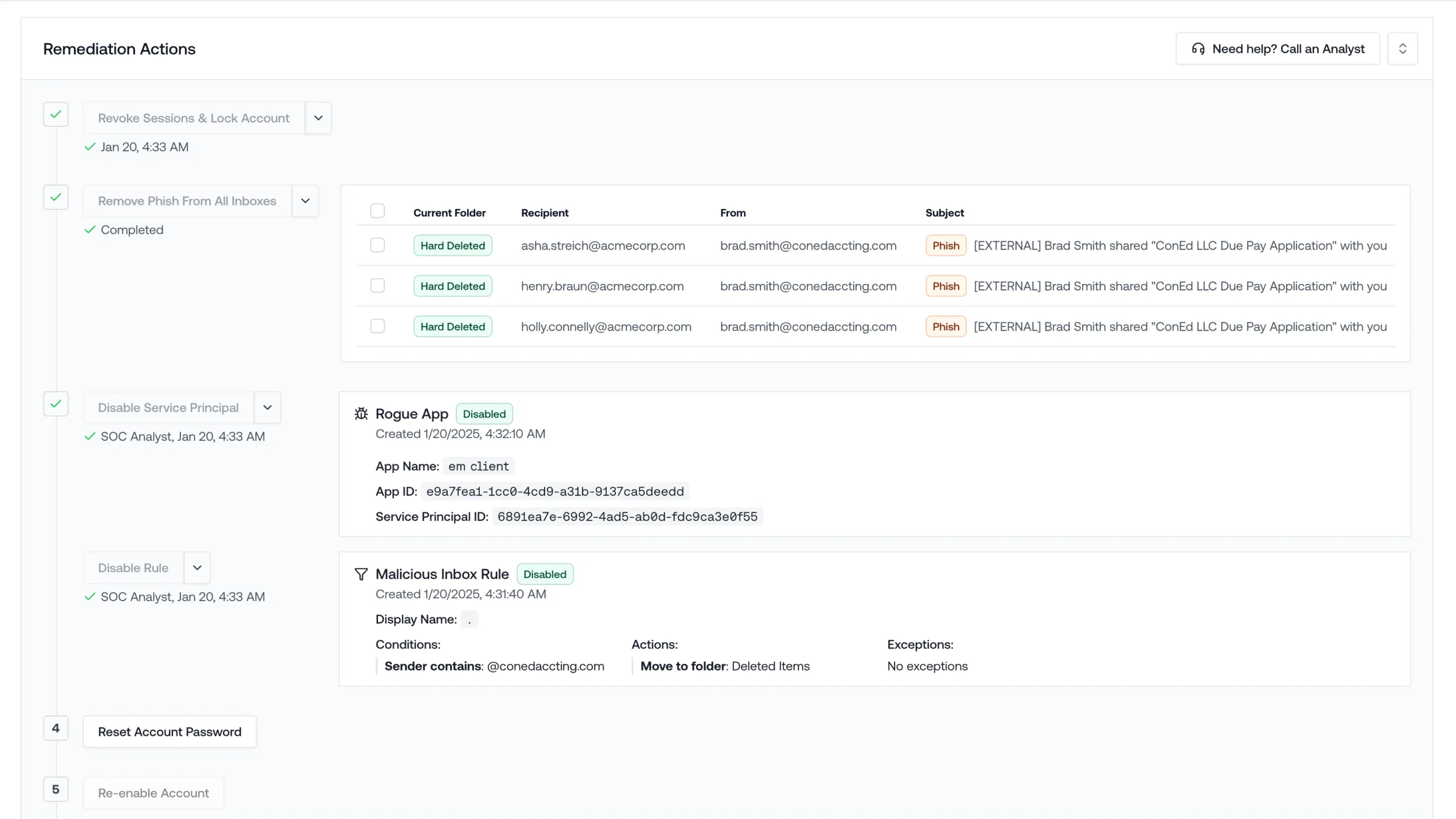
Remediates Everything
An alert is the end of your work, not the beginning.
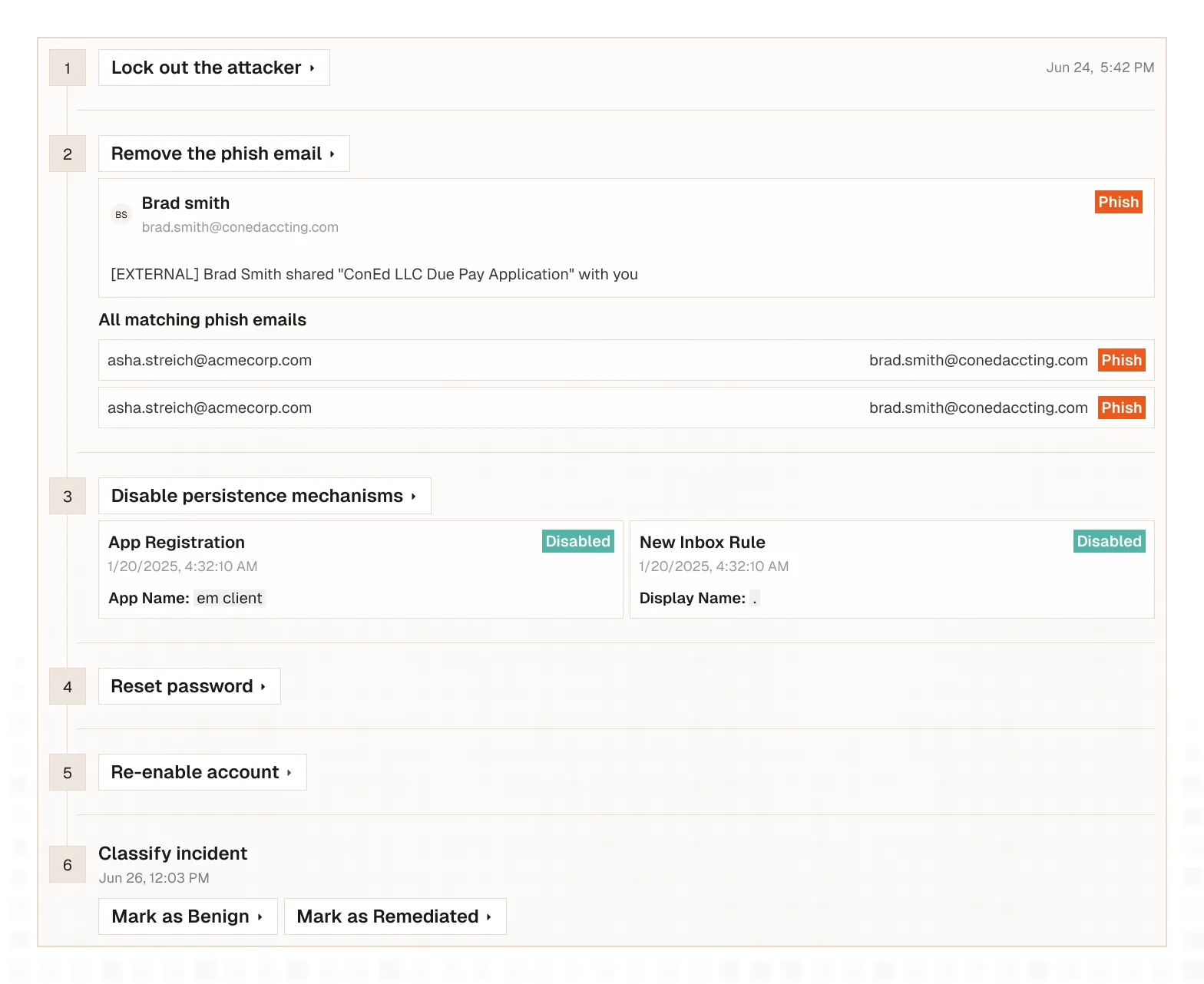
Show Value with Reports
Introducing: Petra Security
Multi-tenant. Only for MSPs.

30-minute Setup. No Tuning Required.

Case Studies
Read about their success stories here:

7 Live Attackers
19 Caught-Late Attackers
6 Caught 2+ Weeks Late
51 Seconds

133 Attacks Stopped with Petra.
6 Total False Alarms.
56 Seconds
90 Hours/Month

29-Day Lurking Attacker Discovered
5 Caught-Late Attackers Discovered
45.9 Days
67.6 Seconds

1 Year
36 Attacks Stopped
2 False Alarms
1 min, 41 secs

19 Attacks Stopped
3 Hours Reclaimed
85% Faster Detection
70% Fewer Alarms

3 Enterprise Deals
1 Year
24 Attacks Stopped
3 mins, 41 secs
Learn about Microsoft security from the best.





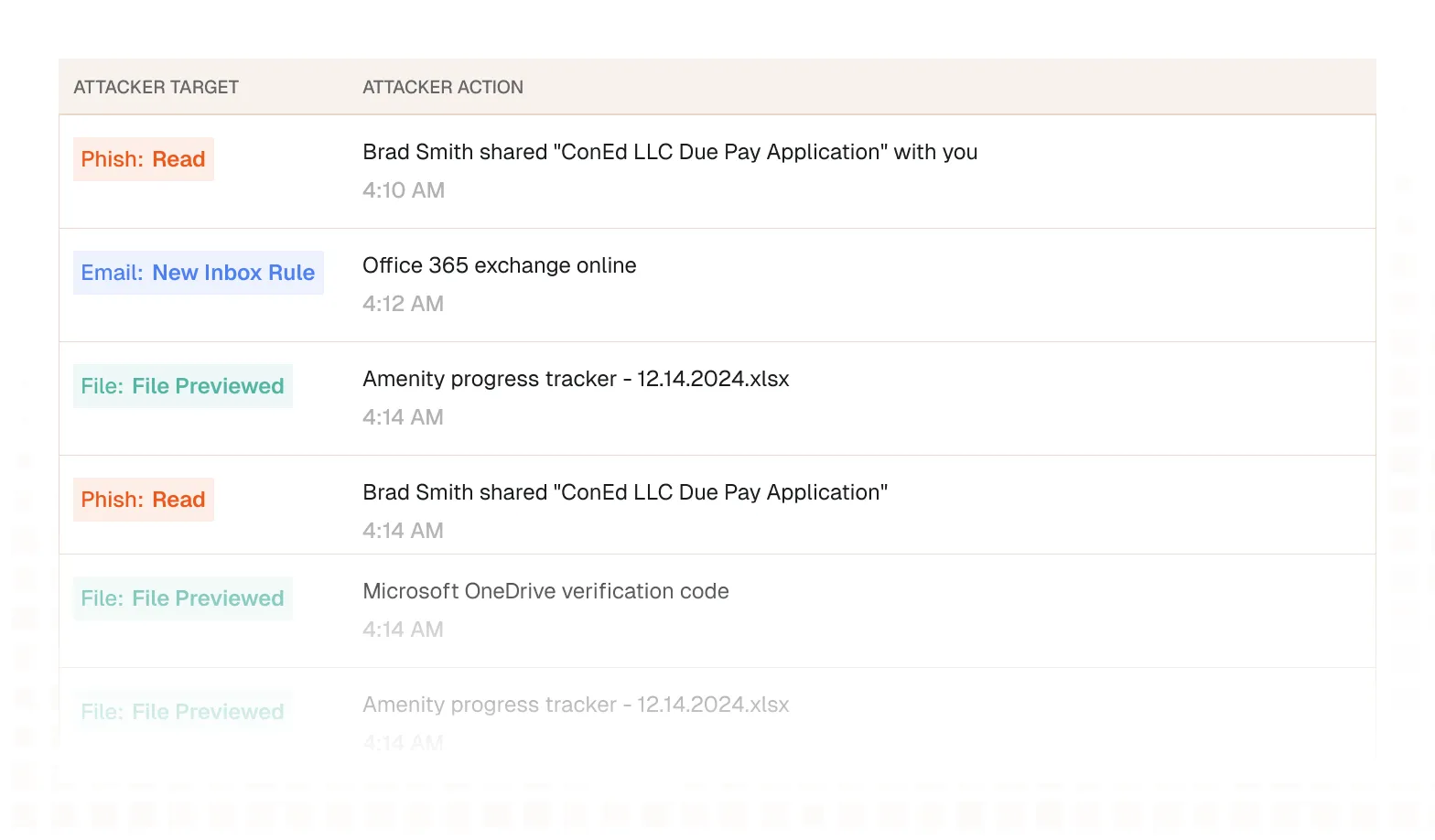
New Data Center Observed in Widespread AitM Attack Campaign

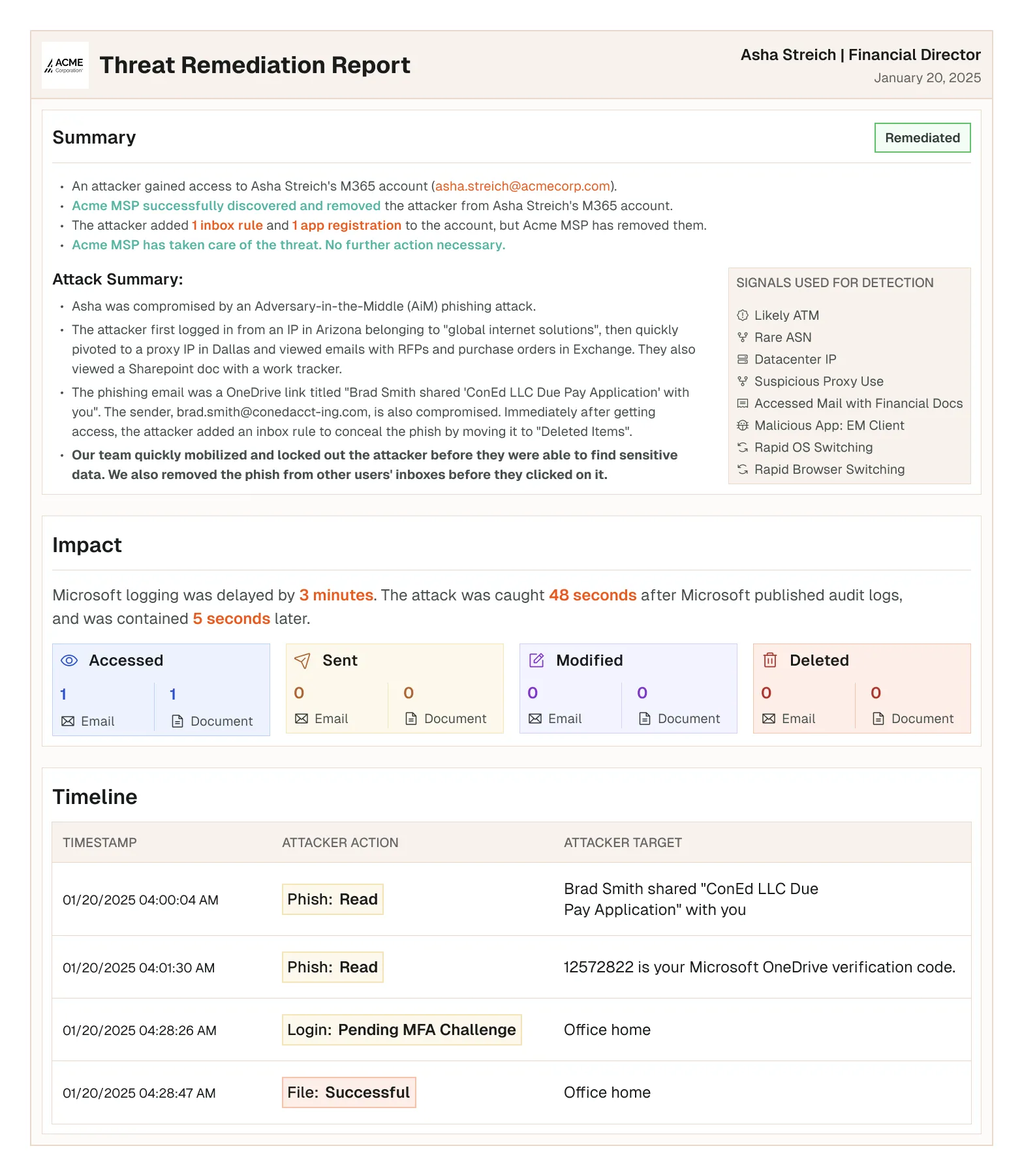
Compromised, then Weaponized: Anatomy of a OneDrive Phishing
Anatomy of a Sophisticated Multi-Infrastructure Password Spray
Convince Your Team
Get a Demo with Petra


















.svg%201.png)














.svg)